Spam and Suspicious Emails
Electronic spamming is the use of electronic messaging systems to send an unsolicited message (spam), especially advertising, as well as sending messages repeatedly on the same site.
While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam.
Source: Wikipedia
For more information on how to keep your email account from being compromised please read the section Email Phishing and Spear-Phishing.
For more information on how to report suspected spam or phishing email please follow the steps outlined in the Webmail, Outlook – Windows, or Outlook – Mac sections.
What is phishing?
Is the attempt to obtain sensitive information such as usernames, passwords, and credit cart details often for malicious reasons by disguising as a trustworthy entity in an email. Phishing is typically carried out by email spoofing and often directs users to enter personal information at a fake website, the look and feel of which are identical to the legitimate one and the only difference is the URL of the website in concern. The goal is to trick the email recipient into believing that the message is something they want or need and to click a link or download an attachment. The information is then used to access important accounts and can result in identity theft or trick users into downloading and installing malware/ransomware.
Spam is the electronic equivalent of the ‘junk mail’ that arrives on your doormat or in your postbox. However, spam is more than just annoying. It can be dangerous – especially if it’s part of a phishing scam.
Spam emails are sent out in mass quantities by spammers and cybercriminals that are looking to do one or more of the following:
* Make money from the small percentage of recipients that actually respond to the message
* Run phishing scams – in order to obtain passwords, credit card numbers, bank account details and more
* Spread malicious code onto recipients’ computers
What is spear phishing?
Spear Phishing is the fraudulent practice of sending emails ostensibly from a known or trusted sender in order to induce targeted individuals to reveal confidential information. Although often intended to steal data for malicious purposes, cybercriminals may also intend to install malware on a targeted user’s computer.
How can I tell if an email is a phishing attempt or not?
Check the Web address to ensure the correct company name and website are correct – DO NOT TRUST THE DISPLAY NAME. Often the web address of a phishing site looks correct but actually contains a common misspelling of the company name or a character/symbol before or after the company name. (for example, www.paypa1.com instead of www.paypal.com).
The three common URLs used by SD42 are:
* sd42.ca – all SD42 branded sites will end in sd42.ca
* office.com – All SD42 email and OneDrive data is being migrated to Microsoft’s Canadian datacenters.
* office365.com – All SD42 email and OneDrive data is being migrated to Microsoft’s Canadian datacenters.
If your SD42 email account is sent an email and you are requested to sign into a website that does not contain any of the above addresses be very cautious. When in doubt go to www.sd42.ca and navigate to the resource you require using the links provided on the sd42 homepage.
These emails often contain links and are requesting you provide personal information. Legit companies do NOT request sensitive information via email.
Additional Phishing Tips
Tip 1: Don’t trust the display name
Check the email address is the header “from”, if it looks suspicious, don’t open the email.
Tip 2: Look but don’t click
Hover your mouse over any links embedded in the body of the email. If the link address looks weird, don’t click on it. If you want to test the link, open a new window and type in website address directly rather than clicking on the link from unsolicited emails.
Tip 3: Check for spelling mistakes
Brands are pretty serious about email. Legitimate messages usually do not have major spelling mistakes or poor grammar. Read your emails carefully and report anything that seems suspicious.
Tip 4: Analyze the salutation
Is the email addressed to a vague “Valued Customer?” If so, watch out—legitimate businesses will often use a personal salutation with your first and last name.
Tip 5: Don’t give up personal information
Legitimate banks and most other companies will never ask for personal credentials via email. Don’t give them up.
Tip 6: Beware of urgent or threatening language in the subject line
Invoking a sense of urgency or fear is a common phishing tactic. Beware of subject lines that claim your “account has been suspended” or your account had an “unauthorized login attempt.”
Tip 7: Review the signature
Lack of details about the signer or how you can contact a company strongly suggests a phish. Legitimate businesses always provide contact details.
Tip 8: Don’t click on attachments
Including malicious attachments that contain viruses and malware is a common phishing tactic. Malware can damage files on your computer, steal your passwords or spy on you without your knowledge. Don’t open any email attachments you weren’t expecting.
Tip 9: Don’t trust the header from email address
Fraudsters not only spoof brands in the display name, but also spoof brands in the header from email address. Return Path found that nearly 30% of more than 760,000 email threats spoofed brands somewhere in the header from email address with more than two thirds spoofing the brand in the email domain alone.
Tip 10: Don’t believe everything you see
Phishers are extremely good at what they do. Just because an email has convincing brand logos, language, and a seemingly valid email address, does not mean that it’s legitimate. Be skeptical when it comes to your email messages—if it looks even remotely suspicious, don’t open it.
What should I do if I think I’m a target of phishing?
1. Contact the IT Department to disable your account and to reset your MyEd BC to a temporary password (if used). This is stop the thousands of outgoing emails being sent on behalf of your account to other users.
2. If provided a District Laptop, this will need to be brought to the IT Dept to be assessed for malware.
3. Contact your admin to advise of situation.
4. If you clicked on a link that directed you to a site that appeared to be your bank, email provider, social media etc, log in to the real site and change your password.
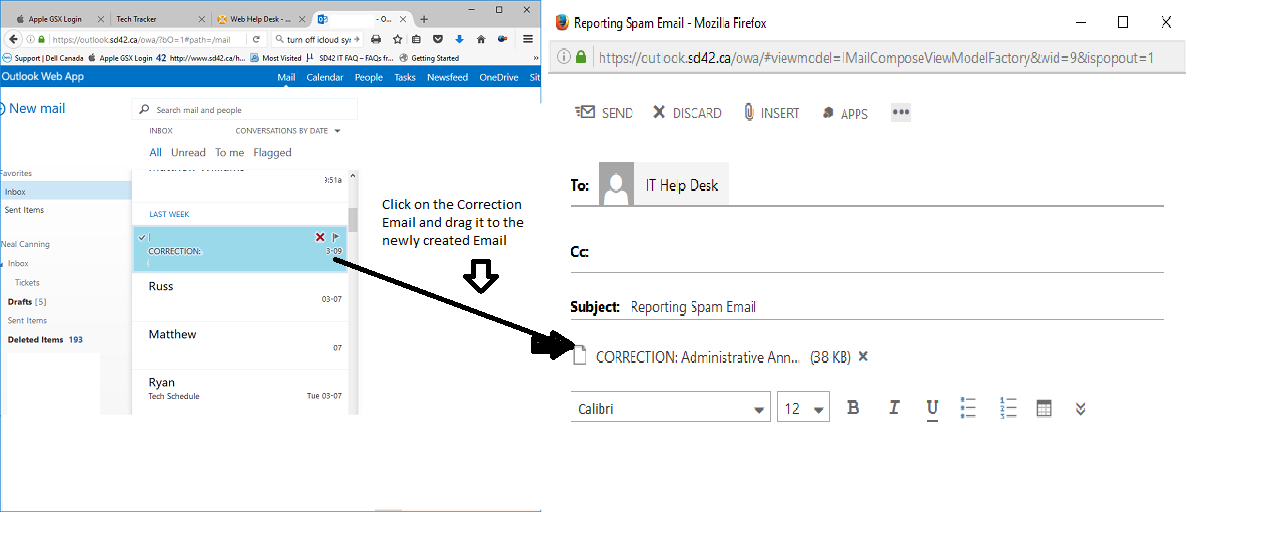
Reporting a suspected spam email using School District No. 42 Webmail
Click on New email. Double click on the new mail in the view pane, which will open it in a separate window. Click and drag on the spam email to the newly created email then send to the IT HelpDesk.
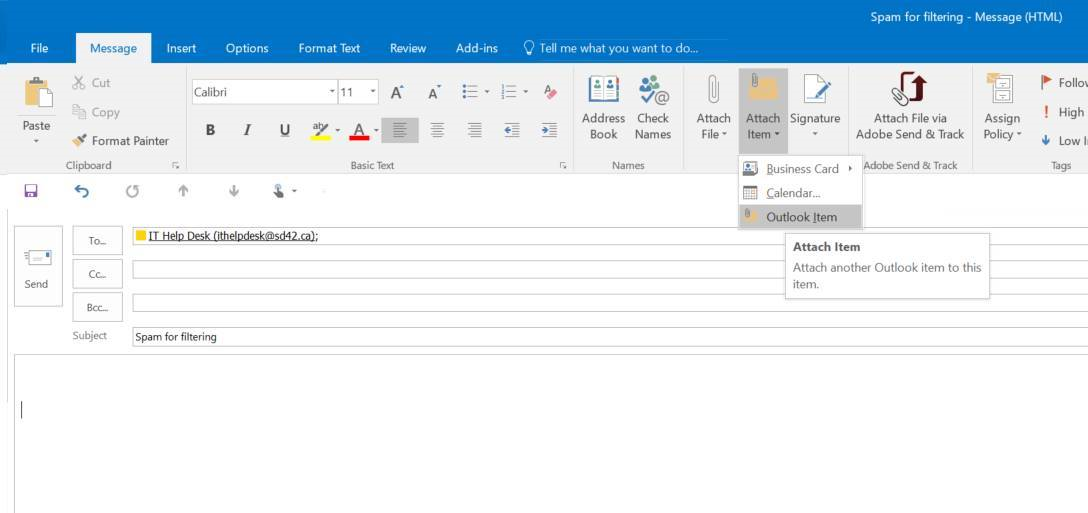
Reporting a suspected spam email using Outlook (Windows)
To forward a suspicious email as an attachment use the following steps:
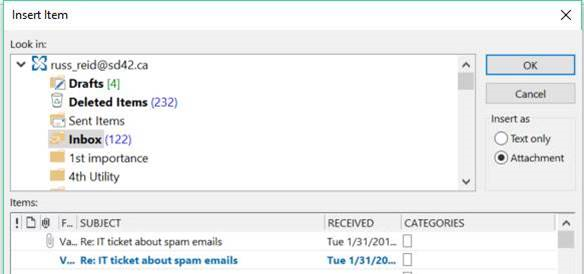
- Open an email in Outlook and then click on attach Outlook Item.
- Then navigate to the suspected spam email and click on it.
- Send it to the IT Helpdesk.
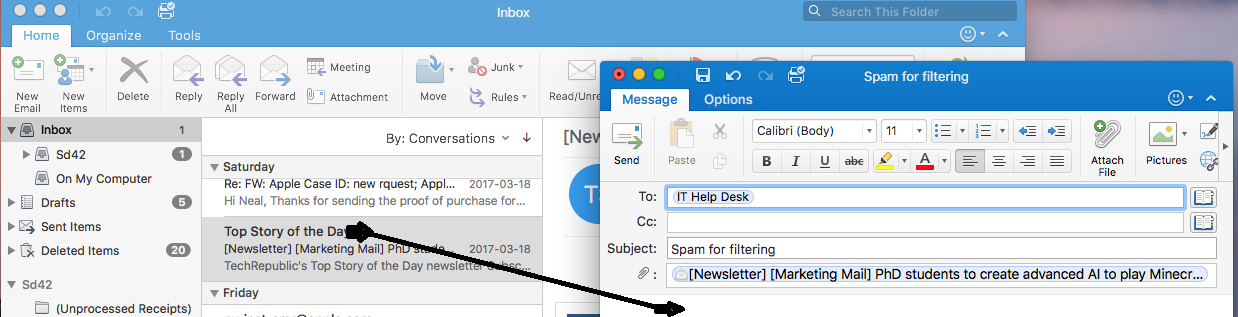
Reporting a suspected spam email using Outlook (Mac)
To forward a suspicious email as an attachment use the following steps:
- Open an email in Outlook, and then click on the suspected spam and drag it into the new email.
- Then in the Subject line type “Spam for filtering.”
- Send it to the IT Helpdesk